Secure secrets configuration and usage
There are three main aspects of the secrets system:
- Configuration of the secret service
- Storing of the secret in some data model
- Accessing the secret from the data model
Configuring the secret service
Configuration of the secret service is done via environment variables, typically in your Tomcat context.xml file. The key and respective values are described in the table below:
| Key | Value |
brightspot/cms/defaultSecretService | The name of the default secret service. This is used in other keys below and is designated as {name}. |
brightspot/cms/secretService/{name}/class | The fully qualified class name of the secret service you would like to use. For example, this would be com.psddev.cms.secret.DatabaseSecretService for the Database Secret Service and com.psddev.aws.secret.AwsSecretService for the AWS Secret Service. |
Individual secret services could require additional configuration. Both the Database Secret Service and AWS Secret Service do require additional configuration.
Storing the secret service
Storage of secrets is done by adding a field to your data model of type com.psddev.cms.secret.Secret. Once this field is added, the Brightspot Secret Service system automatically ensures that any data added by users to this field is encrypted by the default secret service that is configured.
If no default service is configured for the Brightspot instance, the value will be stored as plain text in the database, and the user will be warned that the data is not securely stored. Once a secret service is configured, the data will be securely stored on the next save of the parent object.
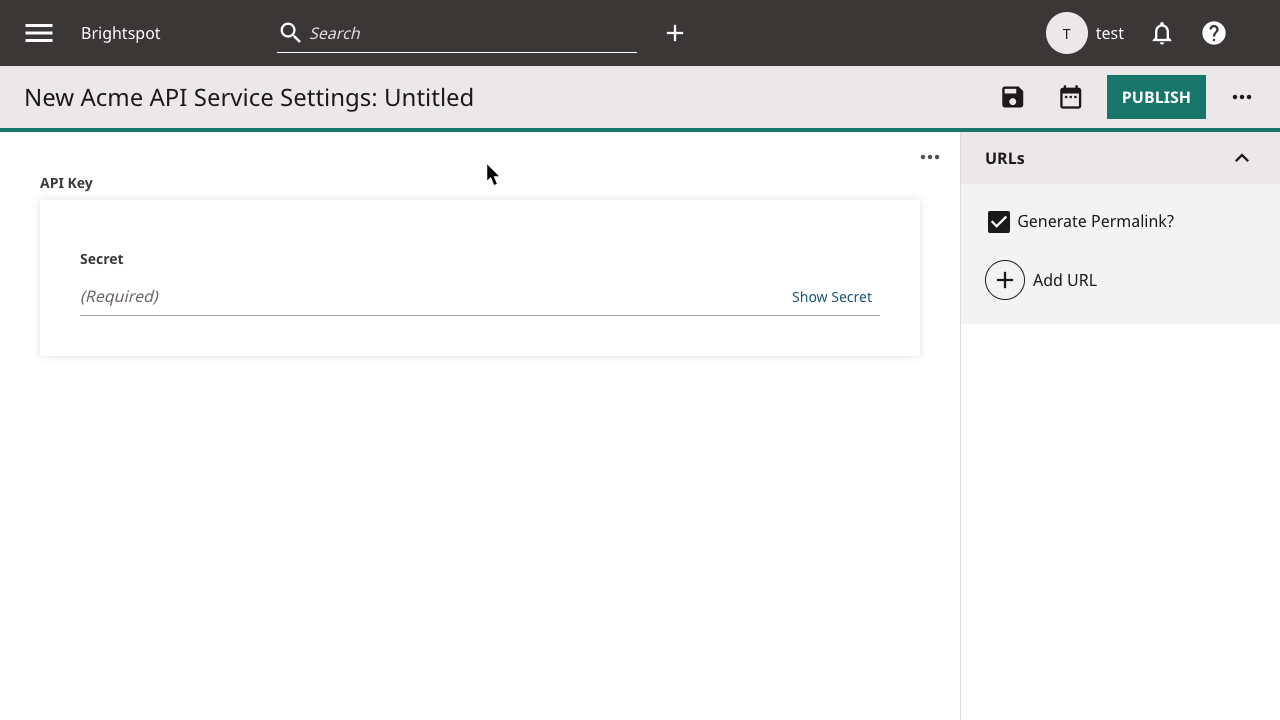
1import com.psddev.cms.secret.Secret;23public class AcmeApiServiceSettings extends Content {45①@DisplayName("API Key")6②@Required7private Secret apiKey;89}
- ①Brightspot annotations can be used on Service fields as usual. Here you can see we change the display name of the field.
- ②Use the
@Requiredannotation to require the input of a value for the field.
Accessing the secret value
Once you have a Secret field on a data model, you can then access the unencrypted value of this secret. This is done by calling Secret#getSecret , which returns the unencrypted value as a string.
1import java.util.Optional;23import com.psddev.cms.secret.Secret;45public class AcmeApiServiceSettings extends Content {67@DisplayName("API Key")8@Required9private Secret apiKey;1011public boolean isValidApiKey(String providedKey) {12return Optional.ofNullable(apiKey)13①.map(Secret::getSecret)14.map(unencryptedSecret -> unencryptedSecret.equals(providedKey))15.orElse(false);16}17}
- ①
Secret#getSecretis called to get the unencrypted value of the secret.